In this article we will tackle the flow of DNS name resolution from equipment running Windows 2000 and later is very important to know-mos this flow, primarily involves troubleshooting.
In pre-Windows 2000 clients, we primarily NetBIOS name resolution that does not necessarily need to be used in Windows 2000 and later systems, which use DNS name resolution as a primary method.
DNS names are divided into two parts as shown below:
WWW. Z1BR.com
ZAMBONIS.Spaces.live.com
COMPUTER01.LOCAL WOODGROVEBANK.
This structure consists of host name (in yellow) and DNS suffix (in red).The host name is associated with a record in DNS that points to an IP address and the DNS suffix associated DNS zone where registry.
Now that we are reminded of how the structure of DNS names, let's look at how the flow of name resolution.
Let's take as an example of a user who wants to access a network share; the user enters \\ServerFS01\SharedFolder
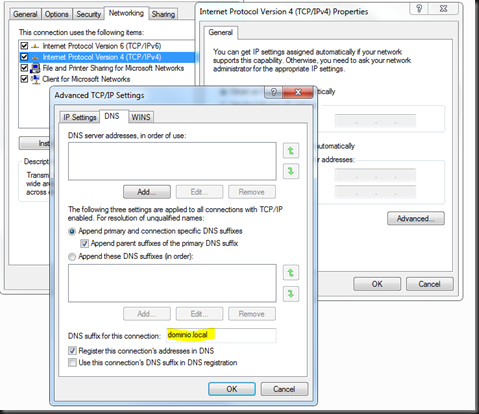
The first step is to complete the requested host name with the DNS suffix of agreement as specified in the network connection properties, clicking on properties of TCP-IP (in both IPv4 and IPv6) version click on the button "Advanced" and the DNS tab as shown in the image:

Is selected by default, the option "Append parent suffixes of the primary DNS Suffix", this option will add the suffix father of MACHINE names requested which was not specified the FQDN, as in our example. Note that below this option we choose in choose a suffix list; in the case of having multiple domains for example (the suffixes are added to the list, in order, until you found the host), with this procedure we can expedite workstation, in a large forest. Another option we configure statically would add a DNS suffix for the connection (this setting will not be changed automatically).
With regard to the primary suffix of the machine, we can find it in the "Advanced properties of the system" in the "computer name" tab, as shown in the picture on below (note that the suffix is by default changed automatically when the machine is joined to a new domain); for security reasons, some organizations desmarcam this checkbox, which can cause name resolution problems if the analyst update manually the primary suffix.

After completing the host name with the DNS suffix, the next system procedure is to check the machine's DNS CACHE function local DNS cache is to expedite the process of resolving names in addition to decrease network traffic; we can see this cache through ipconfig/displaydns command and erases it via ipconfig/flushdns command.
You can disable logging cache through the command net stop DNSCACHE or disabling the DNS Client service by service console (services.msc).
In the local DNS CACHE can be stored records positive responses resolved successfully by the DNS server) and negative records (answers resolved by the DNS server on which the DNS client cannot connect to the host, such as the status of "host not found" when we access a URL. by default, the storage time for a record in the DNS cache is 86,400 seconds (1 day) and a negative record of 900 seconds (15 minutes). However we modify this period by editing the registry:
If the requested name is not resolved by the DNS cache, the next step would be to consult the hosts file located in the directory%windir%\System32\drivers\etc\. The hosts file contains static entries and is typically used to expedite the process of resolving names, pre-population of DNS cache, for environments in "workgroup" as in a DMZ or still to block sites. We use cautiously the hosts file, because it is a way to decentralise the resolution of names; what can cause problems for a resolution, if there are changes in settings of TCP-IP hosts mapped. Below is the video where I show an example of editing the hosts file:
The next step is to forward the request to the preferred DNS server configured on the properties of TCP-IP of the network interface. If the preferred DNS server is offline, or for any reason the DNS client does not have server connectivity, name resolution request is forwarded to the secondary DNS server, if the same is also without communication with the client, the request is forwarded to another DNS server that is listed at the top of the list of DNS servers in the DNS tab of the advanced settings of TCP-IP. The list is checked from top to bottom, what makes recommended placing at the top of the list, the same site and servers, or servers of sites where the link to connect to the DNS client has the highest bandwidth available.

When the request arrives at the DNS server, the server performs the following procedures to try to resolve the host:
1-server's cache (this is not the same DNS cache commented previously, and yes the cache of DNS service);
2 – DNS zones (… search server hosting areas …)
3 – search in the WINS database (if configured …with this feature server searches the database of the WINS servers listed to verify the existence of the requested record.)
4 – conditional forwarders (requisitions routing rules for a given domain DNS)
5 – Forwarders (… forwarding for any request that the server does not resolve)
6 – Root Hints (… servers responsible for the root domain (".") on the Internet)
Note: these DNS server resources will be covered in detail in the next articles in the series