In this article I describe the installation of System Center Configuration Manager 2007 R2 (R2 SCCM2007).
The first step for installation is to meet all the prerequisites for official mesma.Segue links below regarding these requirements:
Supported configurations:
http://technet.microsoft.com/en-us/library/bb680717.aspx
Preparation for the installation of SQL:
http://technet.microsoft.com/en-us/library/bb632649.aspx
Extending Active Directory Schema:
http://technet.microsoft.com/en-us/library/bb633121.aspx
Installation checklist:
http://technet.microsoft.com/pt-br/library/bb680951 (en-us). aspx
Ports used by Configuration Manager
http://technet.microsoft.com/en-us/library/bb632618.aspx
Required settings in firewalls (local or not):
http://technet.microsoft.com/en-us/library/bb694088.aspx
Requirements for Windows Server 2008:
http://technet.microsoft.com/pt-br/library/cc431377 (en-us). aspx
After setting the requirements, we must run the installation DVD Splash.hta SCCM 2007 SP1.Na window appears, we can validate the requirements with the option "Prepare \ Run the prerequisite checker." After the validation of requirements, we will select the option "Install \ Configuration Manager 2007 SP1," as shown in the image below:

At the beginning of the installation, must choose between installing a Site Server installation or the console administração.Iremos choose the installation of Site Server and click Next.

After accepting the license agreement (which is compulsory acceptance for product installation), the next screen we select the options instalação.Temos single option (already pre-determined) and custom (recommended) where we manually configure our parametros.Iremos choose the custom option (as shown in the picture below, and click Next

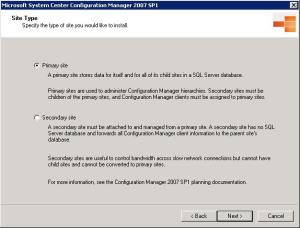
We must choose between installing a Primary Site (site containing a database, required if the first site of a structure SCCM) or Secondary Site (only possible if there is already a primary). How we are performing a new deployment, choose the option to install a Site Primário.Clique Next.
At this stage of installation, we should enable or disable the CEIP to send information to Microsoft (useful for product improvement) and enter the key produto.Após these definitions, we can then choose the path to the installation of SCCM.Após, click Next.
One of the most important steps of the installation is the choice of Site Code and Site Name for this choice is directly related to the design solução.Por this reason, we should always consider a standard and intuitive names that meets the requirements of growth ambiente.Lembrando that the site code and can not be modified or reused.

In the Site window mode, we must establish the operating mode of our estrutura.Devemos choose native mode when we do not have a coexistence of SCCM with SMS 2003, noting that the native mode is required PKI (public key infrastructure) for issuing certificates digitais.Devemos choose the mixed mode when we have a coexistence with SMS 2003, whether the level and server or client, or when we have a public key infrastructure.

After choosing the mode of operation, we select the features that are enabled in instalação.Lembrando that these resources can be enabled after instalação.Após selecting features, click Next.

Enter information regarding the database, SQL server, instance, database ... click Next.

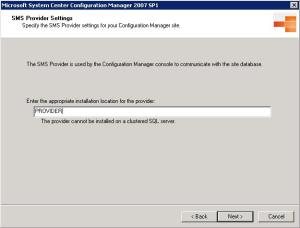
In the window "SMS Provider Settings", we will establish that the SMS PROVIDER will be responsible for reading and writing in the database SCCM.Clique Next. More information about SMS PROVIDER (http://technet.microsoft.com/en -us/library/bb680613.aspx )
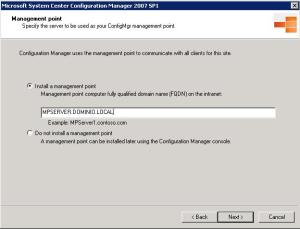
We have this step of the installation to add the role of Management Point to our server or we can choose to add this function later by console.Caso decide to add the function, must enter the FQDN of the server as image abaixo.CliqueNext again.
In the Port Settings window, configure the ports for communication between client / servidor.Por standard HTTP port used is port 80, but we can set up another door qualquer.Clique Next. 
In the next window, the Setup installer will download the prerequisites atualizados.Podemos download the components or can indicate the directory where the components were stored préviamente.Recomendo create directories on the first level and no space in name (eg c: \ SCCM) as shown below, Next.

Enter the directory path where the components will be armasenados.CliqueNext.

This displays a summary of the settings and start the installation process.
After finishing the installation process for SCCM 2007 SP1 (recommended restarting the server!), We will start the installation of SCCM 2007 R2.From the installation media, we run the Splash.hta and in the window, select the" Install \ Configuration Manager 2007 R2. "

To start the installation process, click Next in the window "Welcome" and in the "Installation".

Click Finish to end the installation.

After installation of SCCM 2007 R2, it would be interesting to test the operation of the console, create the install directories, verification services, installation logs, etc..